How do you ensure the security and privacy of VoIP calls?
June 11, 2025Voice over Internet Protocol (VoIP) is a cloud-based phone system that sends and receives calls through an internet connection.
VoIP phone systems are an attractive communication solution for businesses. Its functionality and cost-effectiveness have made it popular among small and large companies alike. So, it is essential to ensure the security and privacy of VoIP calls to save your business from huge losses.
This article touches upon the importance of VoIP security and common security threats. We will also discover how to make VoIP calls as secure as possible.
Importance of VoIP Security
A survey carried out among risk management experts showed that cyber incidents are the most common risks to businesses in 2023. Data breaches are very dangerous. They can lead a business to bankruptcy
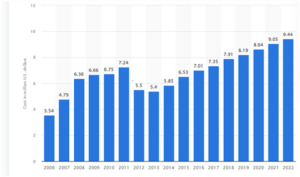
The average cost of data breaches in the US was 9.44 Million US Dollars in the year 2022. This is a considerable rise compared to the numbers of the previous year. In 2021, the average cost per data breach was 9.05 Million dollars.
Many small businesses fail to recover from a data breach. One study found that as many as 60% of small businesses have to call it quits within 6 months of a cyber attack.
Cyber security is one of the top concerns of business owners. If you are switching from traditional landline communication to VoIP calls, you must ensure it is secure and safe.
What are the Common VoIP Security Risks?
Distributed Denial of Service (DDOS) Attacks
The attacker overwhelms the server with data and uses up all of its bandwidth. This results in denial of service i.e. users can’t use their VoIP phone services.
DDOS attacks are usually done through bots that flood the network with connection requests or data which makes the system inoperable.
Call Tampering
Call tempering refers to the disruption of an ongoing call. Although call tempering is not as serious as other security threats, it is very bothersome.
The hijacker accesses the call stream and disrupts it by injecting additional noise packets. It becomes impossible to communicate in the presence of noise.
Vishing Scam Calls
Vishing is VoIP-based phishing. Hijackers make calls to seek important information like passwords and credit card numbers.
VoIP Fraud
The intruder uses your VoIP phone system and collects the revenue. Toll fraud is VoIp fraud in which the hijacker makes numerous international calls through your VoIP system.
Their goal is to get a share of the revenue generated by these calls. It is also known as International revenue sharing fraud (IRSF).

Malware and Viruses
Malware and viruses cause a lot of problems in the VoIP system. VoIP needs an excellent internet connection to work properly and the viruses consume network bandwidth and cause signal congestion. This security threat affects the quality of calls as the signal keeps breaking down.
These malicious programs can also result in packet loss. Moreover, they can make your system vulnerable to more damage by creating Trojan backdoors. These backdoors serve as entry points for intruders by bypassing authentication procedures.
How to Keep Your VoIP Network Secure?
You can ensure the security and privacy of calls by following the best practices.
Use Strong Passwords and two-factor authentication
You must ensure that your password is strong. It is advisable to change the passwords frequently.
Avoid using the same password for different accounts and encourage your employees to do so.
Moreover, work passwords should not include any personal information like home addresses.
Perform Security Assessment Regularly
A security breach that stays unnoticed does more damage than anything. You must perform security audits to detect and prevent attacks. It is recommended to hire an independent security agency to conduct a thorough security audit. The following things must be checked in a security audit.
● Firewall Performance: Ensure that the firewall is configured and can weed out hijackers. The firewall works well if no data packets are lost before reaching the target destination.
● Assessment of Patching Procedures: Ensure that both hardware and software of the VoIP system are not prone to Cyber attacks.
● Application Security: All applications used by the business must be thoroughly scanned. If you detect any security in an application, stop using it until the issue is resolved.
● Gateway Checks: VoIP gateways must have an effective security system in place
● Cyberattack Simulations: The security agency should test the ability of the VoIP system to detect and prevent any attempt of a data breach.
How to Choose the Right VoIP Provider?
The most crucial step towards ensuring the security and privacy of VoIP calls is choosing the best VoIP service provider. You can’t achieve your security goals simply by following VoIP best practices. VoIP providers and users must contribute to ensure a secure and safe communication system.
Consider the following factors before choosing a VoIP provider.:
Security Certifications
Your VoIP service provider must have all relevant security certifications. Some of the important ones are the following:
● Service Organization Compliance (SOC): The American Institute of CPAs created SOC2 to ensure secure data management. SOC2 criteria for managing customer data based on 5 trust service principles.
● Payment Card Industry Compliance (PCI): It helps ensure secure online payments through the card.
● HIPAA Compliance: It makes sure that patient data is well-kept and safe from intruders. It goes on to include voice notes and call recordings.
● ISO/IEC 20071 Compliance: This ensures that all security controls are effective and updated recently.
End-to-End Encryption
Ask the provider if they encrypt the data properly. Find out how the data is being encrypted. Sometimes encryption of data deteriorates the quality of the calls.
Staff Competency
Ensure that the staff of the VoIP service provider is regularly trained and retrained. No online system is completely resistant to cyber-attacks. The team of such a service provider must be vigilant and knowledgeable to face new challenges confidently.
Conclusion
In conclusion, VoIP is an efficient calling system as long as it is private and secure. Good VoIP practices help businesses to protect their data and systems from attack. You can ensure the security and privacy of your business calls by educating yourself about the problems and their solutions. If you are still trying to figure out where to start, seek our professional help from Venom IT to assess your risks and put in place the appropriate controls. Together, we can keep your business safe from security breaches.
Related News


4 min read
6 min read


7 min read